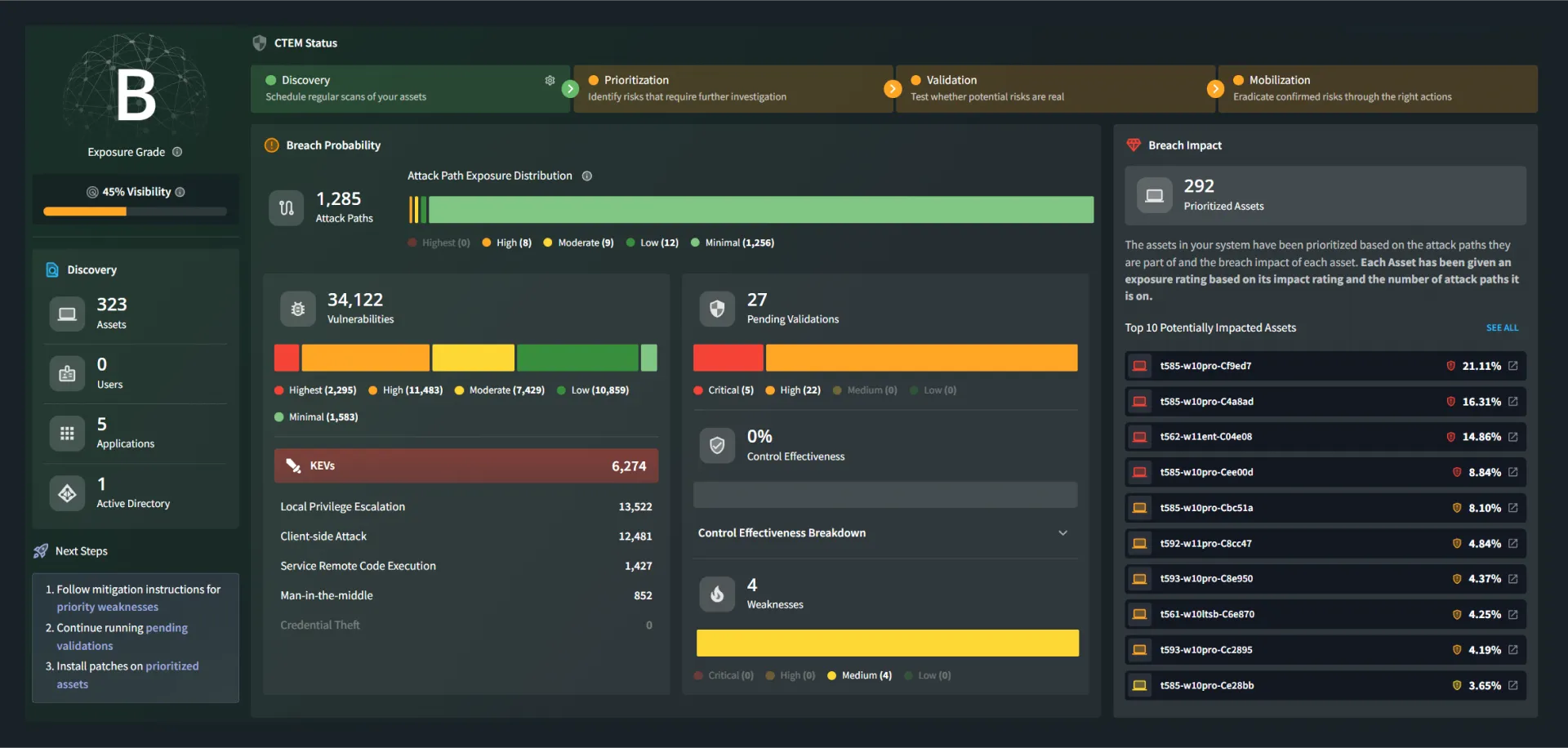
How Do You Manage Exposure?
You can’t manage what you can’t measure.
Validate everything.
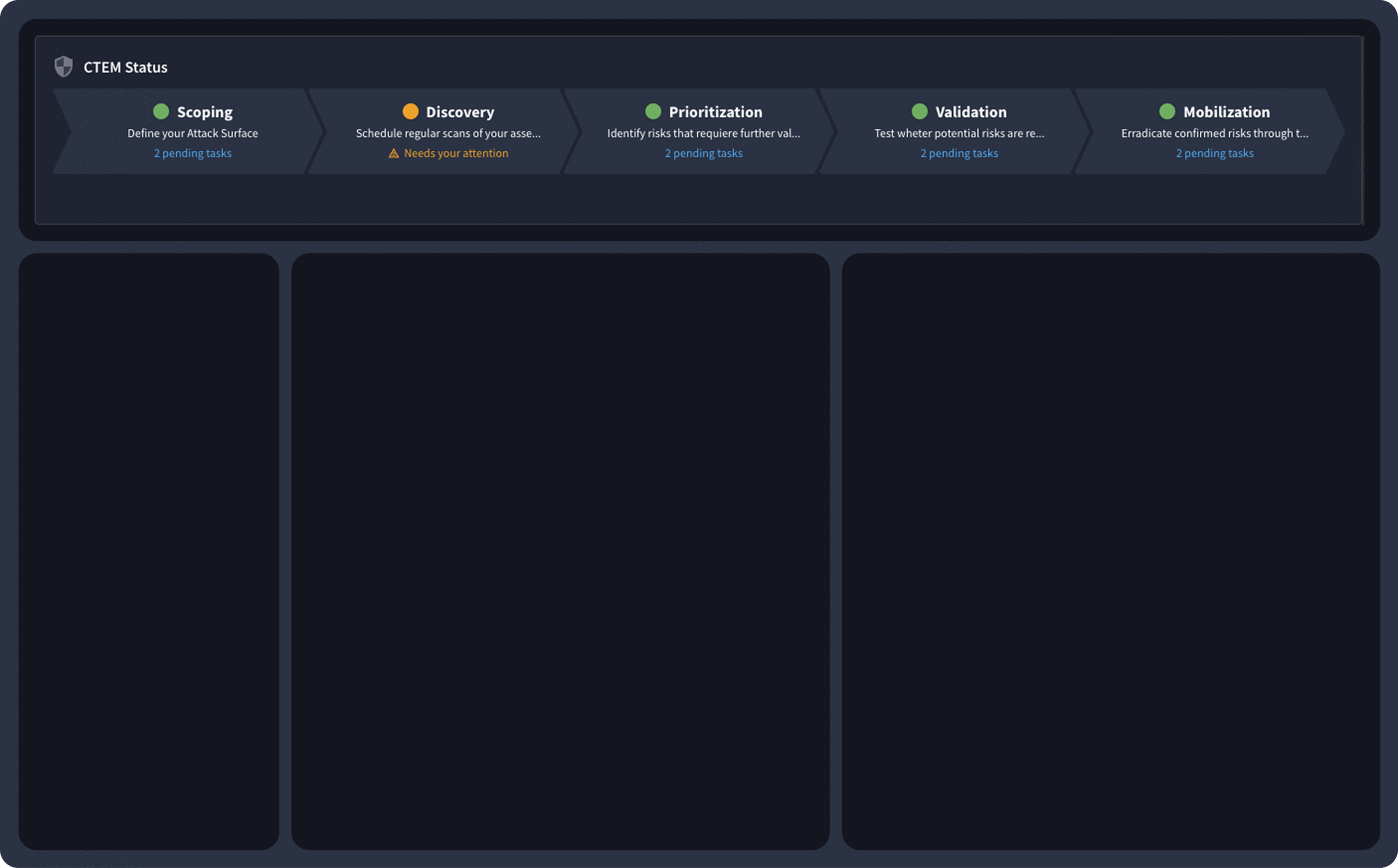
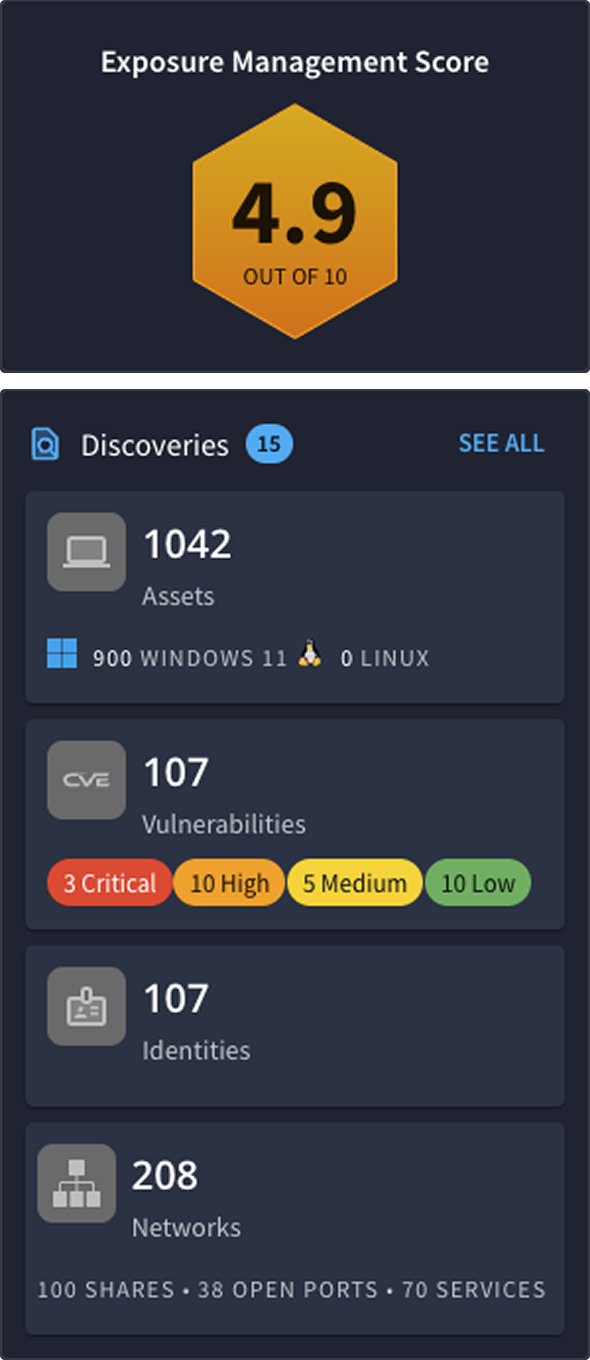
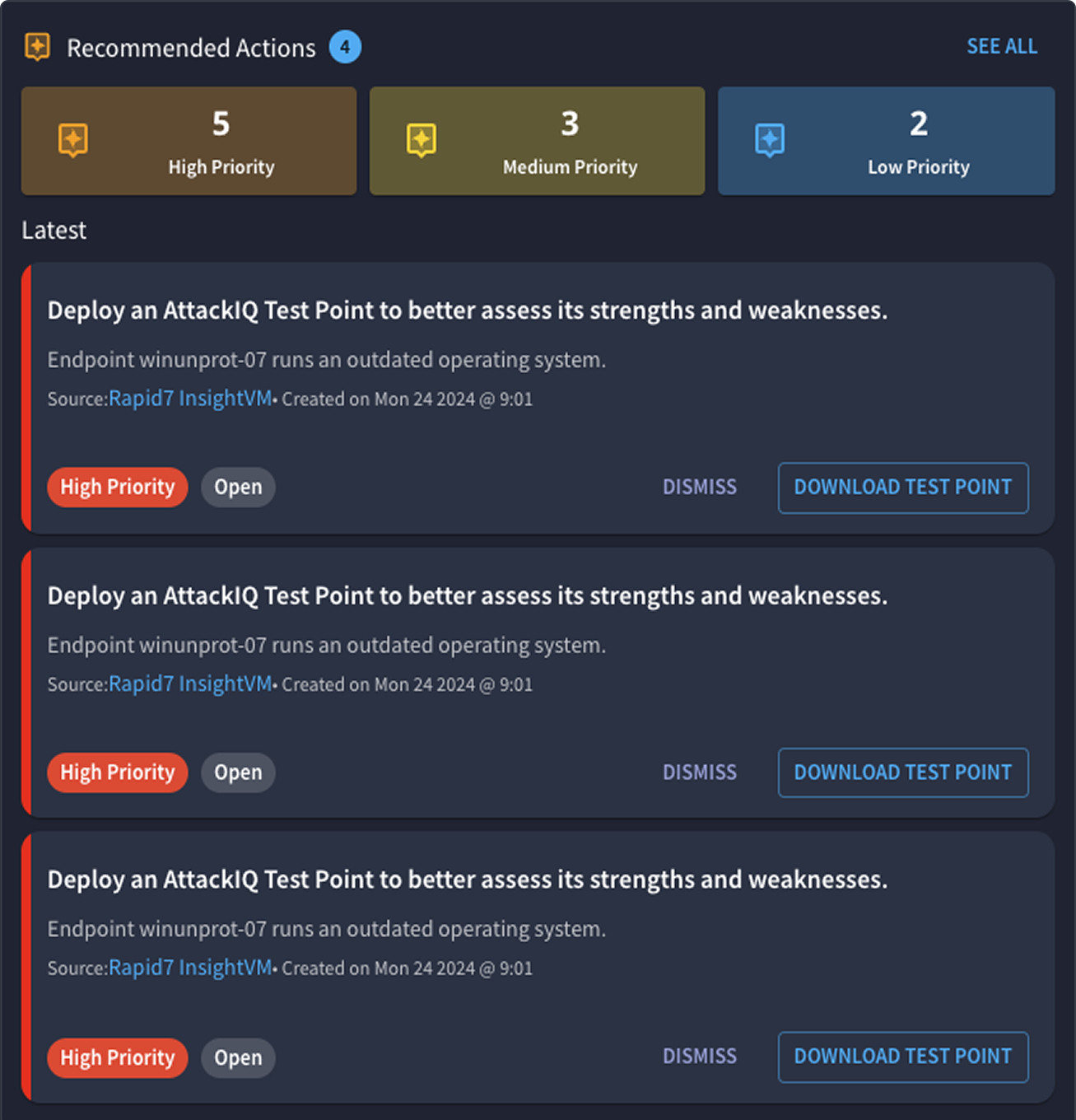

AEV: The Next Evolution of BAS
Validate Continuously
Catch failures fast with always-on, automated testing that eliminates point-in-time blind spots.
Validate Everything
Verify threats, controls, and attack paths across cloud, identity, and infrastructure—in one unified platform.
Validate Everywhere
Evaluate defenses across endpoints, hybrid environments, and third parties at scale and without disruption.
Validate What Matters
Prioritize exploitable exposures that impact your business and prove which defenses actually work.
Introducing The AttackIQ Adversarial Exposure Validation (AEV) Platform
The AttackIQ AEV platform goes beyond traditional exposure management by continuously validating security controls and simulating real-world scenarios.
Proactively Manage Threat Exposure with CTEM + AEV
AEV puts CTEM into action—helping you uncover control failures, reduce exposure, and close security gaps before attackers can exploit them. The result is stronger defenses, lower risk, and improved operational performance.
Align Security With Business Priorities
Smarter Security, Proven Results
Gain unparalleled visibility, efficiency, and control for unmatched protection, cost savings, and peace of mind.
Be Ready for Every Threat,
Every Time
Achieve continuous resilience through a proactive, threat-informed defense.
Optimize Defensive Posture
Reduce
Exposure
featured Resource
10 Strategic Priorities for Security Leaders in 2026
AI acceleration and industrialized cybercrime are changing the threat landscape. Learn what security leaders must operationalize now to build resilience in 2026.
Read the Guide
Real Impact for Real-World
Security Challenges
From Fortune 500 companies to mid-sized enterprises, organizations across industries trust us to keep them resilient.
Never Settle for Uncertainty
Validate Your Defenses
Take the guesswork out of threat exposure management. Validate your defenses with real-world attack scenarios and focus on what matters most—managing your risk.